Sophos firewall backup cmd from CLI & How to copied backup to USB or https or FTP & pull certificate from XG
Zitat von mpachmann am 15. Oktober 2024, 15:19 Uhrhttps://community.sophos.com/sophos-xg-firewall/f/discussions/141743/sophos-firewall-backup-cmd-from-cli-how-to-copied-backup-to-usb-or-https-or-ftp-method-with-detailed-steps-for-download-backup-these-use-while-gui-hardware-failure-in-some-reason
Backup of the configurations via CLI with the following command: /bin/opcode system_backup -s nosync
and the back up can be found under the following directory: var/conf/backupdata/You can use either FTP CLI Command or vis WINSCP Software
FTP CLI COMMAND:
curl --insecure --ftp-ssl ftp://ftp.sophos.com:990 -u <username>:<password> -T '<directory>'
curl --insecure --ftp-ssl ftp://ftp-insecure.sophos.com -u <username>:<password> -T '<directory>'You can use ftpput to upload files to an FTP server:
ftpput -u username -p password ftp.server.com /path/to/upload/file.logftpput -u sophostransfer@avanet.com -p UrXPMmGYXtAsaX6?LnAJx3fgrK www.avanet.com strongswan.log
- ftpput: Transfers a file to an FTP Server.
- -u username -p password: Authenticates with the specified FTP login data.
- ftp.server.com: Address of the FTP Server.
- /path/to/upload/file.log: Path to the local file to be uploaded.
Alternatively, you can also use the curl command to upload files to an FTP:
curl --ftp-ssl ftp://www.avanet.com -u sophostransfer@avanet.com:Ur$tAs3fg46rK -v -T {/tmp/ips.log,/tmp/applog.log,/tmp/csc.log,/tmp/u2d.log}WINSCP: https://support.sophos.com/support/s/article/KB-000042152?language=en_USPSCP
- Download PuTTY.
- Open command prompt and find PSCP.
- Copy the log file from your firewall to your device, in Windows, for example, by running the following command:
pscp -scp admin@:Example: (privkey.ppk from putty keyring)
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.pem c:\Users\user\Documents\certs\SOPHOSImport\
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.key c:\Users\user\Documents\certs\SOPHOSImport\
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.tar.gz c:\Users\user\Documents\certs\SOPHOSImport\
In the tar.gz File is the password for the private key. If you pull the certificate over curl (https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Certificates/HowToArticles/CertificatesAPIGetCertificate/index.html) then the private Key is exported without password.
If you are receiving a permission error when running the command, copy the contents from
log/totmp/then correct your command's source.Example:
cp log/syslog.log* var/dataThe asterisk (*) allows you to also collect the newly archived versions. If you compress them, for example, with the command
tar -zcvf var/log_archive.tar.gz var/data, it results in a smallertmp/log_archive.tar.gzfile but with proper permissions.You can also go to Advanced Shell and run the command
cpExample:
cp /log/VPN.log Users\Noah\Desktop- Enter your admin password.
To Access the Firewall with public-key authentication
https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Administration/DeviceAccess/index.html#local-service-acl-how-device-access-workshttps://techbast.com/2018/11/sophos-firewall-how-to-set-up-public-key-authentication-for-admin.html
Overview
- This article describes the steps to configure public key authentication for admin account.
Generate an RSA key pair
- Download and install both PuTTY and PuTTYGen from www.putty.org.
- Open PuTTYGen and select SSH-2 RSA (or RSA in newer version of PuTTYGen) and click Generate.
- Save the public and private key
- Note: PuTTYGen will generate a warning if your keylife isn’t protected by a password. Password protected is recommended as an additional security meansure, but not required for SSH to work.
- If you’d like to set a password, enter it in the Key Passphrase and repeat it in the Confirm Passphrase fields prior to clicking Save private key.
Add the public key to Sophos Firewall
- Copy the public key from PuTTYGen or from it’s saved location and go to Administrator -> Device Access. Add this public key under Public Key Authentication section.
Add the private key to PuTTY and authenticate to Sophos Firewall
- Start PuTTY and go to Connection -> SSH -> Auth.
- Click Browse to select the .ppk keyfile generated earlier.
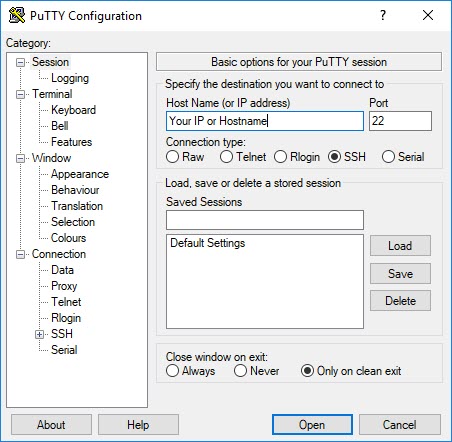
- Navigate to Session and enter the Sophos Firewall’s IP address or hostname.
- Make sure Connection type is set to SSH and click Open to connect to Sophos Firewall.
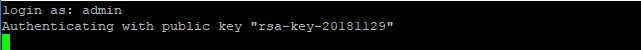
- Enter the name admin to authenticate to Sophos firewall.
Unpack tar.gz. file
tar -zxvf filename.tar.gz --directory destination-folderConvert pem and key file to pfx
openssl pkcs12 -inkey mycert.key -in mycert.pem -export -out mycert.pfx -passin file:privkeypasswordfile.txt -passout pass:
Backup of the configurations via CLI with the following command: /bin/opcode system_backup -s nosync
and the back up can be found under the following directory: var/conf/backupdata/
You can use either FTP CLI Command or vis WINSCP Software
FTP CLI COMMAND:
curl --insecure --ftp-ssl ftp://ftp.sophos.com:990 -u <username>:<password> -T '<directory>'
curl --insecure --ftp-ssl ftp://ftp-insecure.sophos.com -u <username>:<password> -T '<directory>'
You can use ftpput to upload files to an FTP server:
ftpput -u username -p password ftp.server.com /path/to/upload/file.logftpput -u sophostransfer@avanet.com -p UrXPMmGYXtAsaX6?LnAJx3fgrK www.avanet.com strongswan.log- ftpput: Transfers a file to an FTP Server.
- -u username -p password: Authenticates with the specified FTP login data.
- http://ftp.server.com: Address of the FTP Server.
- /path/to/upload/file.log: Path to the local file to be uploaded.
Alternatively, you can also use the curl command to upload files to an FTP:
curl --ftp-ssl ftp://www.avanet.com -u sophostransfer@avanet.com:Ur$tAs3fg46rK -v -T {/tmp/ips.log,/tmp/applog.log,/tmp/csc.log,/tmp/u2d.log} WINSCP: https://support.sophos.com/support/s/article/KB-000042152?language=en_USPSCP
- Download PuTTY.
- Open command prompt and find PSCP.
- Copy the log file from your firewall to your device, in Windows, for example, by running the following command:
pscp -scp admin@:Example: (privkey.ppk from putty keyring)
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.pem c:\Users\user\Documents\certs\SOPHOSImport\
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.key c:\Users\user\Documents\certs\SOPHOSImport\
pscp -scp -unsafe -i privkey.ppk admin@SOPHOSIP:/conf/certificate/*.tar.gz c:\Users\user\Documents\certs\SOPHOSImport\In the tar.gz File is the password for the private key. If you pull the certificate over curl (https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Certificates/HowToArticles/CertificatesAPIGetCertificate/index.html) then the private Key is exported without password.
If you are receiving a permission error when running the command, copy the contents from
log/totmp/then correct your command's source.Example:
cp log/syslog.log* var/dataThe asterisk (*) allows you to also collect the newly archived versions. If you compress them, for example, with the command
tar -zcvf var/log_archive.tar.gz var/data, it results in a smallertmp/log_archive.tar.gzfile but with proper permissions.You can also go to Advanced Shell and run the command
cpExample:
cp /log/VPN.log Users\Noah\Desktop - Enter your admin password.
To Access the Firewall with public-key authentication
https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Administration/DeviceAccess/index.html#local-service-acl-how-device-access-works
Sophos Firewall: How to set up public key authentication for admin
Overview
- This article describes the steps to configure public key authentication for admin account.
Generate an RSA key pair
- Download and install both PuTTY and PuTTYGen from http://www.putty.org.
- Open PuTTYGen and select SSH-2 RSA (or RSA in newer version of PuTTYGen) and click Generate.
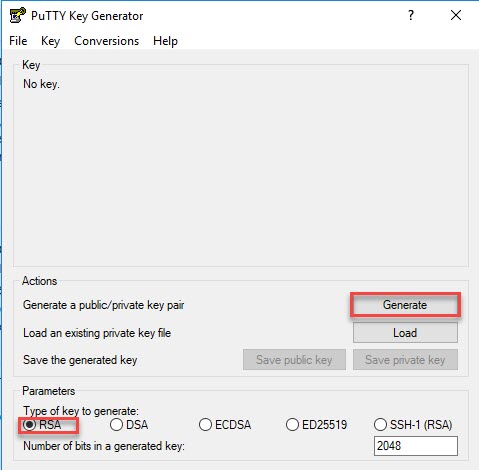
- Save the public and private key
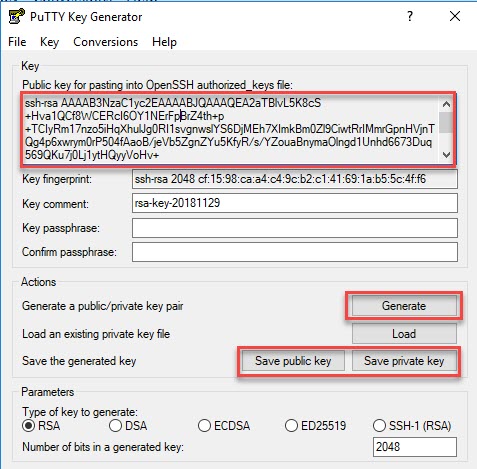
- Note: PuTTYGen will generate a warning if your keylife isn’t protected by a password. Password protected is recommended as an additional security meansure, but not required for SSH to work.
- If you’d like to set a password, enter it in the Key Passphrase and repeat it in the Confirm Passphrase fields prior to clicking Save private key.
Add the public key to Sophos Firewall
- Copy the public key from PuTTYGen or from it’s saved location and go to Administrator -> Device Access. Add this public key under Public Key Authentication section.
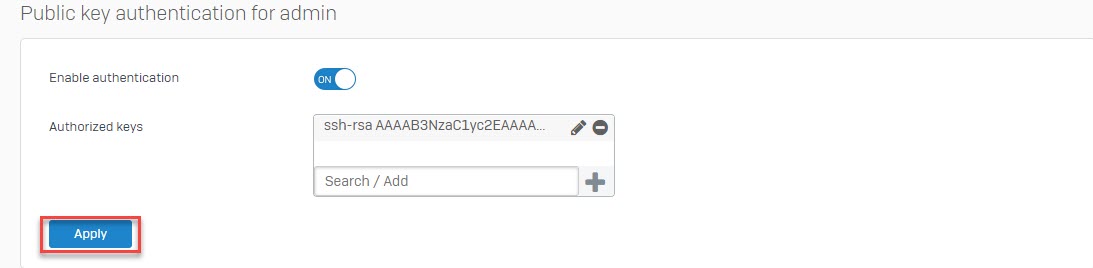
Add the private key to PuTTY and authenticate to Sophos Firewall
- Start PuTTY and go to Connection -> SSH -> Auth.
- Click Browse to select the .ppk keyfile generated earlier.
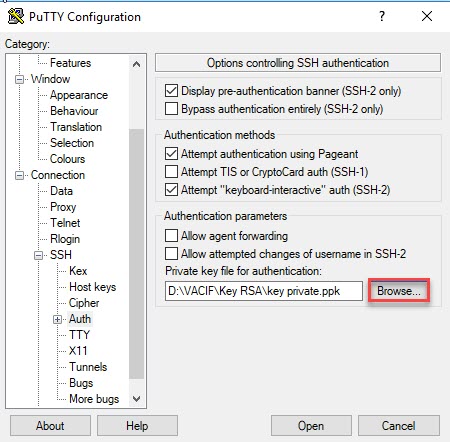
- Navigate to Session and enter the Sophos Firewall’s IP address or hostname.
- Make sure Connection type is set to SSH and click Open to connect to Sophos Firewall.
- Enter the name admin to authenticate to Sophos firewall.
Unpack tar.gz. file
tar -zxvf filename.tar.gz --directory destination-folder
Convert pem and key file to pfx
openssl pkcs12 -inkey mycert.key -in mycert.pem -export -out mycert.pfx -passin file:privkeypasswordfile.txt -passout pass:

